Which Of The Following Firewall Architectures Is Designed To Host Servers That Offer Public Services
More than xxx years later on the concept of the network firewall entered the security conversation, the technology remains an essential tool in the enterprise network security armory. A mechanism to filter out malicious traffic before it crosses the network perimeter, the firewall has proven its worth over the decades. Only, every bit with whatsoever essential technology used for a lengthy period of time, developments have helped advance both the firewall's capabilities and its deployment options.
The firewall traces dorsum to an early period in the modern net era when systems administrators discovered their network perimeters were being breached by external attackers. There was destined to be some sort of process that looked at network traffic for clear signs of incidents.
Steven Bellovin, and then a fellow at AT&T Labs Research and currently a professor in the computer science section at Columbia University, is generally credited -- although not by himself -- with start using the term firewall to describe the process of filtering out unwanted network traffic. The proper name was a metaphor, likening the device to partitions that keep a fire from migrating from i part of a physical structure to another. In the networking case, the idea was to insert a filter of sorts between the ostensibly safety internal network and whatever traffic entering or leaving from that network's connectedness to the broader internet.
The term has grown gradually in familiar usage to the point that no coincidental chat about network security can take place without at least mentioning it. Along the way, the firewall has evolved into dissimilar types of firewalls.
This article somewhat arbitrarily argues that there are five central types of firewalls that use different mechanisms to identify and filter out malicious traffic, but the exact number of options is not nearly as important as the idea that different kinds of firewall products do rather dissimilar things. In improver, enterprises may need more than one of the five firewalls to ameliorate secure their systems. Or one single firewall may provide more than 1 of these firewall types. There are likewise iii different firewall deployment options to consider, which we will explore in farther detail.
5 types of firewall include the following:
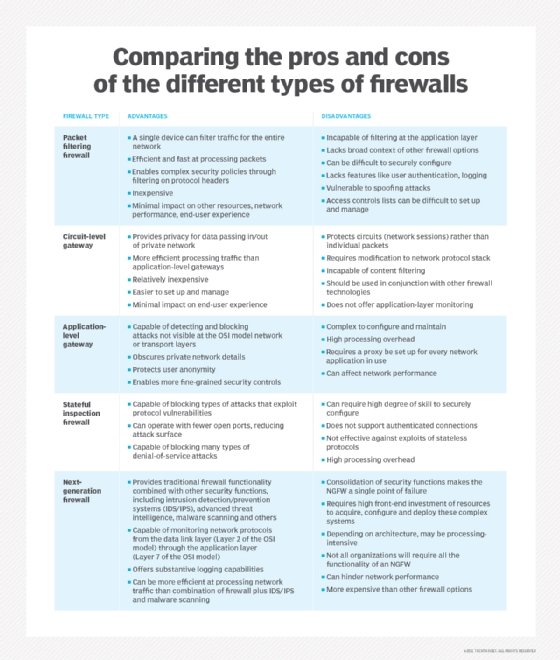
- packet filtering firewall
- excursion-level gateway
- application-level gateway (aka proxy firewall)
- stateful inspection firewall
- next-generation firewall (NGFW)
Firewall devices and services can offering protection across standard firewall part -- for example, past providing an intrusion detection or prevention arrangement (IDS/IPS), deprival-of-service (DoS) attack protection, session monitoring, and other security services to protect servers and other devices within the private network. While some types of firewalls tin can work every bit multifunctional security devices, they need to exist part of a multilayered compages that executes effective enterprise security policies.
How do the dissimilar types of firewalls work?
Firewalls are traditionally inserted inline beyond a network connection and await at all the traffic passing through that point. Every bit they practice then, they are tasked with telling which network protocol traffic is benign and which packets are part of an attack.
Firewalls monitor traffic against a ready of predetermined rules that are designed to sift out harmful content. While no security product tin can perfectly predict the intent of all content, advances in security technology make it possible to apply known patterns in network data that take signaled previous attacks on other enterprises.
All firewalls apply rules that define the criteria under which a given packet -- or ready of packets in a transaction -- can safely be routed forward to the intended recipient.
Here are the 5 types of firewalls that continue to play meaning roles in enterprise environments today.
1. Packet filtering firewall
Packet filtering firewalls operate inline at junction points where devices such as routers and switches do their work. Still, these firewalls don't route packets; rather they compare each package received to a prepare of established criteria, such as the allowed IP addresses, parcel blazon, port number and other aspects of the packet protocol headers. Packets that are flagged as troublesome are, generally speaking, unceremoniously dropped -- that is, they are not forwarded and, thus, cease to be.
Packet filtering firewall advantages
- A single device can filter traffic for the entire network
- Extremely fast and efficient in scanning traffic
- Inexpensive
- Minimal effect on other resources, network operation and finish-user experience
Packet filtering firewall disadvantages
- Because traffic filtering is based entirely on IP accost or port information, packet filtering lacks broader context that informs other types of firewalls
- Doesn't bank check the payload and can be easily spoofed
- Not an platonic option for every network
- Access control lists can be difficult to set up and manage
Packet filtering may not provide the level of security necessary for every use example, but there are situations in which this low-cost firewall is a solid option. For minor or budget-constrained organizations, packet filtering provides a basic level of security that can provide protection against known threats. Larger enterprises can as well use package filtering as office of a layered defense to screen potentially harmful traffic between internal departments.
two. Circuit-level gateway
Using another relatively quick way to identify malicious content, excursion-level gateways monitor TCP handshakes and other network protocol session initiation letters across the network every bit they are established betwixt the local and remote hosts to determine whether the session being initiated is legitimate -- whether the remote system is considered trusted. They don't audit the packets themselves, withal.
Circuit-level gateway advantages
- Only processes requested transactions; all other traffic is rejected
- Easy to set and manage
- Depression cost and minimal impact on end-user feel
Circuit-level gateway disadvantages
- If they aren't used in conjunction with other security technology, excursion-level gateways offering no protection against information leakage from devices within the firewall
- No application layer monitoring
- Requires ongoing updates to go on rules current
While circuit-level gateways provide a higher level of security than package filtering firewalls, they should be used in conjunction with other systems. For instance, excursion-level gateways are typically used alongside application-level gateways. This strategy combines attributes of packet- and excursion-level gateway firewalls with content filtering.
3. Application-level gateway
This kind of device -- technically a proxy and sometimes referred to equally a proxy firewall -- functions as the only entry point to and leave signal from the network. Application-level gateways filter packets non only according to the service for which they are intended -- as specified by the destination port -- but also past other characteristics, such every bit the HTTP asking string.
While gateways that filter at the awarding layer provide considerable data security, they tin dramatically bear upon network performance and can exist challenging to manage.
Application-level gateway advantages
- Examines all communications between outside sources and devices behind the firewall, checking non just accost, port and TCP header information, but the content itself before it lets any traffic pass through the proxy
- Provides fine-grained security controls that can, for instance, allow access to a website merely restrict which pages on that site the user can open
- Protects user anonymity
Application-level gateway disadvantages
- Can inhibit network performance
- Costlier than some other firewall options
- Requires a high caste of endeavor to derive the maximum benefit from the gateway
- Doesn't work with all network protocols
Application-layer firewalls are best used to protect enterprise resource from web application threats. They can both block admission to harmful sites and forestall sensitive information from beingness leaked from within the firewall. They tin can, however, introduce a delay in communications.
4. Stateful inspection firewall
State-aware devices not only examine each bundle, just also keep rails of whether or not that packet is part of an established TCP or other network session. This offers more security than either bundle filtering or circuit monitoring alone simply exacts a greater toll on network performance.
A further variant of stateful inspection is the multilayer inspection firewall, which considers the menses of transactions in process across multiple protocol layers of the seven-layer Open Systems Interconnection (OSI) model.
Stateful inspection firewall advantages
- Monitors the entire session for the country of the connectedness, while also checking IP addresses and payloads for more than thorough security
- Offers a loftier degree of command over what content is let in or out of the network
- Does non demand to open numerous ports to allow traffic in or out
- Delivers substantive logging capabilities
Stateful inspection firewall disadvantages
- Resource-intensive and interferes with the speed of network communications
- More than expensive than other firewall options
- Doesn't provide authentication capabilities to validate traffic sources aren't spoofed
Most organizations benefit from the use of a stateful inspection firewall. These devices serve as a more thorough gateway between computers and other assets within the firewall and resources across the enterprise. They as well can be highly effective in defending network devices against item attacks, such as DoS.

5. Next-generation firewall
A typical NGFW combines package inspection with stateful inspection and besides includes some variety of deep packet inspection (DPI), as well every bit other network security systems, such every bit an IDS/IPS, malware filtering and antivirus.
While bundle inspection in traditional firewalls looks exclusively at the protocol header of the package, DPI looks at the actual data the packet is carrying. A DPI firewall tracks the progress of a web browsing session and tin notice whether a bundle payload, when assembled with other packets in an HTTP server reply, constitutes a legitimate HTML-formatted response.
NGFW advantages
- Combines DPI with malware filtering and other controls to provide an optimal level of filtering
- Tracks all traffic from Layer two to the application layer for more accurate insights than other methods
- Can exist automatically updated to provide current context
NGFW disadvantages
- In order to derive the biggest do good, organizations demand to integrate NGFWs with other security systems, which can be a complex process
- Costlier than other firewall types
NGFWs are an essential safeguard for organizations in heavily regulated industries, such as healthcare or finance. These firewalls deliver multifunctional adequacy, which appeals to those with a strong grasp on just how virulent the threat environment is. NGFWs work best when integrated with other security systems, which, in many cases, requires a high degree of expertise.
Firewall delivery methods
As IT consumption models evolved, and then besides did security deployment options. Firewalls today tin can be deployed as a hardware appliance, be software-based or be delivered equally a service.
Hardware-based firewalls
A hardware-based firewall is an apparatus that acts as a secure gateway between devices inside the network perimeter and those outside it. Because they are self-independent appliances, hardware-based firewalls don't consume processing power or other resources of the host devices.
Sometimes called network-based firewalls, these appliances are ideal for medium and large organizations looking to protect many devices. Hardware-based firewalls require more cognition to configure and manage than their host-based counterparts.
Software-based firewalls
A software-based firewall, or host firewall, runs on a server or other device. Host firewall software needs to be installed on each device requiring protection. As such, software-based firewalls swallow some of the host device's CPU and RAM resource.
Software-based firewalls provide individual devices meaning protection confronting viruses and other malicious content. They tin discern different programs running on the host, while filtering inbound and outbound traffic. This provides a fine-grained level of control, making it possible to enable communications to/from ane programme but foreclose it to/from another.
Cloud/hosted firewalls
Managed security service providers (MSSPs) offer cloud-based firewalls. This hosted service tin can be configured to track both internal network activity and third-party on-need environments. Also known as firewall every bit a service, cloud-based firewalls tin can be entirely managed past an MSSP, making it a good option for large or highly distributed enterprises with gaps in security resources. Cloud-based firewalls tin as well be beneficial to smaller organizations with limited staff and expertise.
Which firewall is best for your enterprise?
Choosing the right type of firewall ways answering questions about what the firewall is protecting, which resource the arrangement tin can afford and how the infrastructure is architected. The all-time firewall for one organisation may not be a good fit for another.
Bug to consider include the following:
- What are the technical objectives for the firewall? Can a simpler product work better than a firewall with more features and capabilities that may not exist necessary?
- How does the firewall itself fit into the organization's compages? Consider whether the firewall is intended to protect a low-visibility service exposed on the internet or a web awarding.
- What kinds of traffic inspection are necessary? Some applications may crave monitoring all packet contents, while others tin can simply sort packets based on source/destination addresses and ports.
Many firewall implementations incorporate features of different types of firewalls, and then choosing a type of firewall is rarely a matter of finding one that fits neatly into whatever particular category. For example, an NGFW may incorporate new features, along with some of those from bundle filtering firewalls, application-level gateways or stateful inspection firewalls.
Choosing the ideal firewall begins with understanding the architecture and functions of the individual network being protected but also calls for agreement the dissimilar types of firewalls and firewall policies that are most effective for the organization.
Whichever blazon(s) of firewalls you choose, keep in listen that a misconfigured firewall can, in some ways, be worse than no firewall at all because it lends the unsafe false impression of security, while providing niggling to no protection.
This was last published in January 2021
Which Of The Following Firewall Architectures Is Designed To Host Servers That Offer Public Services,
Source: https://www.techtarget.com/searchsecurity/feature/The-five-different-types-of-firewalls
Posted by: duongshateriere.blogspot.com


0 Response to "Which Of The Following Firewall Architectures Is Designed To Host Servers That Offer Public Services"
Post a Comment