Why Might You Need To Use The Service Password-encryption Command? What Does It Encrypt?
Like many systems administrators out there, I've often plant myself with tasks eligible for automation. Automating is great with PowerShell until you need to pass credentials into a script.
I have seen many administrators put passwords into the trunk of their script. For testing purposes, this could considered a forgivable law-breaking. In production scripts, putting your passwords in obviously view is non only a bad affair…information technology'due south a terrifying thing. It should be a central sin. But you tin can secure a password with PowerShell (or at least reduce password visibility).
First, nosotros'll learn how to supply a credential without having to save it pants-downward plain-text in your script for all the globe (or your role) to see.
Get-Credential and Read-Host
You can create a PSCredential object with the Get-Credential cmdlet, and store the output into a variable. You tin can then pass that variable into whatever cmdlet that supports PSCredential objects.
$MyCredential = Get-Credential
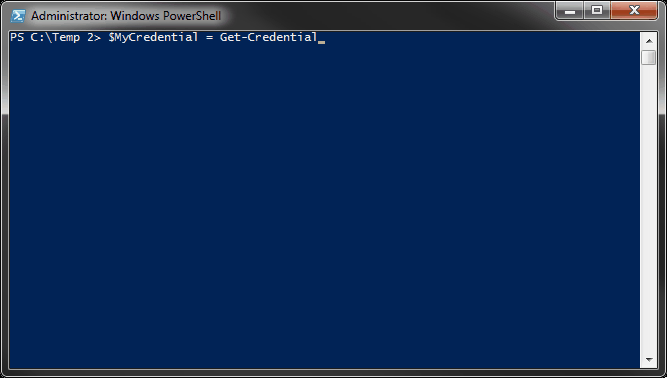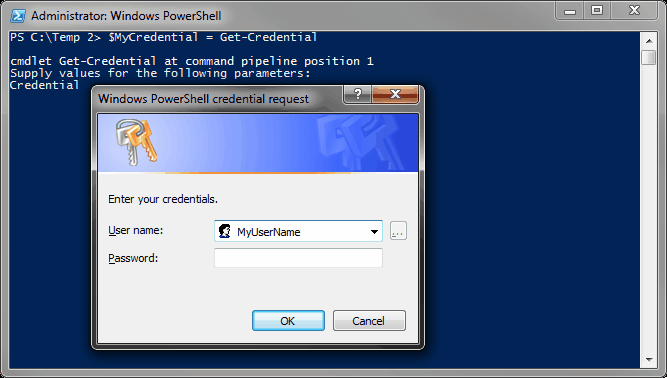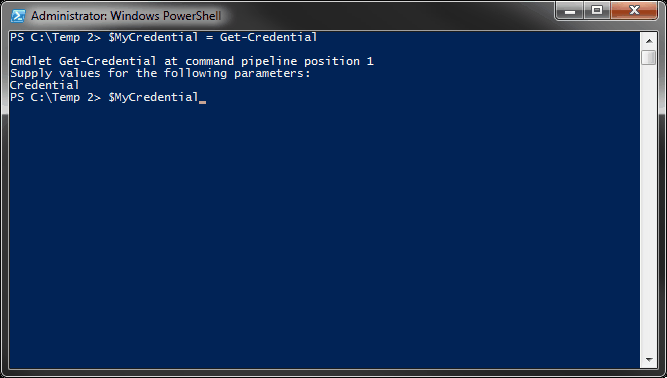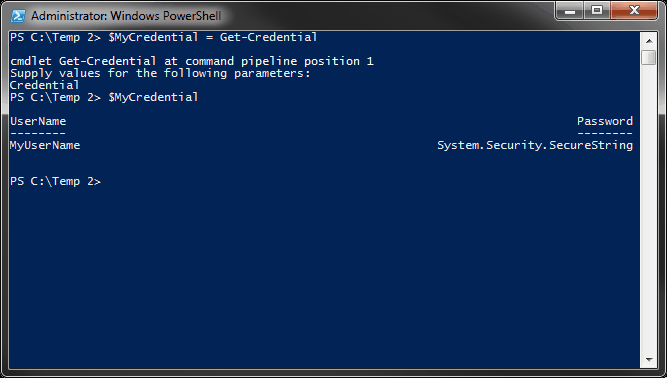
Notice that when y'all access the variable $MyCredential, you are able to come across the username simply not the password. It only displays, "System.Security.SecureString" on the screen. This is because the password is at present stored as a SecureString.
You can and then use this new PSCredential object with cmdlets that support PSCredential objects. You can also individually reference the username or the countersign for cmdlets that don't accept a PSCredential object just will support username and password parameters.
In those cases, you can use $MyCredential.Username and $MyCredential.Username
Or yous can use Read-Host to prompt for input and store the result in a variable. This includes prompting for a SecureString (for a password).
$user = Read-Host "Enter Username" $pass = Read-Host "Enter Password" -AsSecureString
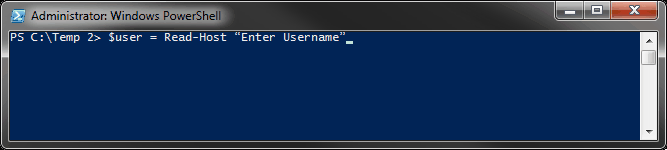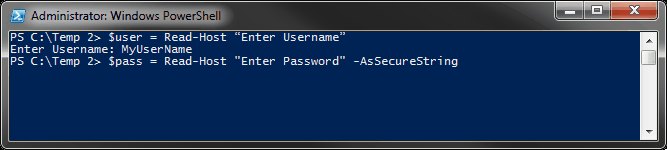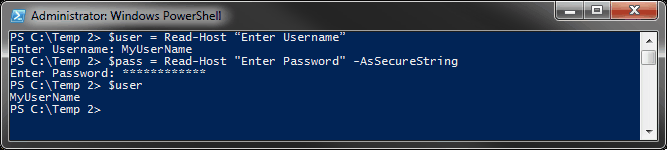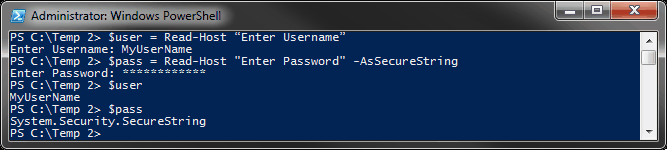
The output is very similar to the output of the Get-Credential variable we used, $MyCredential. Information technology shows the username as "MyUserName" and the countersign as "Arrangement.Security.SecureString."
This is great for manual runs of scripts as it helps to remove the password from the script, only it doesn't really help with our automation. We're looking for a solution that volition be able to run automatically without having to constantly supply credentials via Get-Credential/Read-Host or by leaving our passwords in obviously view for anybody to read.
ConvertTo-SecureString – Encrypting passwords and other strings
Use ConvertTo-SecureString to convert manifestly text or encrypted standard strings into a SecureString object. The SecureString object can exist used with cmdlets that support parameters of type SecureString, as is the case with a PSCredential object. You lot can use the command to ascertain a variable, or piping results into the command.
Syntax: ConvertTo-SecureString [-String] SomeString ConvertTo-SecureString [-String] SomeString [-SecureKey SecureString] ConvertTo-SecureString [-Cord] SomeString [-Central Byte[]] ConvertTo-SecureString [-Cord] SomeString [-AsPlainText] [-Force] –Cord String The string to convert to a SecureString –SecureKey SecureString Encryption primal equally a SecureString. –Key Byte[] Encryption key as a byte array. –AsPlainText Tells control to treat string as plain text. The cord is not encrypted when using this command. Because of the lack of security, the -Force parameter is besides required. –Force Confirms you empathize the lack of security when using -AsPlainText
When you are non using the –Central or –SecureKey parameters, PowerShell uses the Windows Data Protection API to encrypt/decrypt your strings. This effectively ways that only the same user account on the same computer volition be able to use this encrypted string. That is something to continue in mind as yous endeavour to automate any scripts. If you're using a service account, you'll need to employ the –Primal or -SecureKey parameters.
Permit's say you lot desire to accept the text "P@ssword1" and convert it to a SecureString. Since this is a plain text cord, nosotros're going to apply the –AsPlainText and –Force parameters.
"P@ssword1" | ConvertTo-SecureString -AsPlainText -Strength
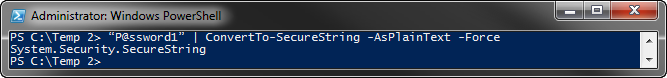
The result is a SecureString object. Unfortunately, yous cannot save a SecureString object to a file for later apply. You have to convert this SecureString object to an encrypted standard string. You tin do this with ConvertFrom-SecureString.
ConvertFrom-SecureString – Saving encrypted standard strings
Utilize ConvertFrom-SecureString to catechumen secure strings into encrypted standard strings. Y'all can use the control direct or pipe results into the command.
Syntax: ConvertFrom-SecureString [-SecureString] SecureString ConvertFrom-SecureString [-SecureString] SecureString [-SecureKey SecureString] ConvertFrom-SecureString [-SecureString] SecureString [-Fundamental Byte[]] –String String The string to catechumen to a SecureString –SecureKey SecureString Encryption key as a SecureString. –Central Byte[] Encryption central as a byte assortment.
Post-obit the aforementioned case higher up, we'll take the output of the previous example and pipe it into the ConvertFrom-SecureString command to get an encrypted standard string.
"P@ssword1" | ConvertTo-SecureString -AsPlainText -Force | ConvertFrom-SecureString
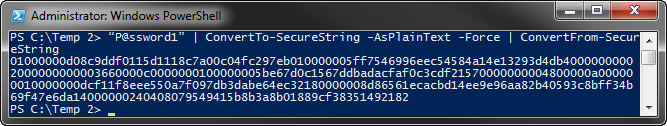
The result is an encrypted standard string that yous can and so save for later retrieval.
Putting it all together
We at present know how to convert a SecureString to an encrypted standard cord. We can take any method we like to go a SecureString, convert it to a standard cord and then salvage information technology to a file. Here is an case of each:
Exporting SecureString from Plain text with Out-File
"P@ssword1" | ConvertTo-SecureString -AsPlainText -Force | ConvertFrom-SecureString | Out-File "C:\Temp 2\Password.txt"
Exporting SecureString from Get-Credential
(Become-Credential).Password | ConvertFrom-SecureString | Out-File "C:\Temp two\Password.txt"
Exporting SecureString from Read-Host
Read-Host "Enter Password" -AsSecureString | ConvertFrom-SecureString | Out-File "C:\Temp ii\Password.txt"
Whatever one of these examples should provide you with a Password.txt file that has an encrypted standard string the represents the password.
When you need to use this encrypted password, you simply reverse the process by importing the data from your file and utilise ConvertTo-SecureString. If all you demand is a SecureString, you can cease there. You lot could even take it a step further and create a PSCredential object.
Creating SecureString object with Become-Content and ConvertTo-SecureString
$pass = Go-Content "C:\Temp ii\Password.txt" | ConvertTo-SecureString
Creating PSCredential object
$User = "MyUserName" $File = "C:\Temp 2\Password.txt" $MyCredential=New-Object -TypeName Organisation.Direction.Automation.PSCredential ` -ArgumentList $User, (Get-Content $File | ConvertTo-SecureString)
Final notes
This will not stop anybody who knows what they're doing from decrypting your password or from reusing your encrypted countersign if they ever are able to compromise your login. The whole betoken of converting your password to a SecureString and storing it in a file is to keep it out of plain text in your scripts so that it's non equally easily discovered. It'southward not foolproof, merely it's pretty practiced.
As mentioned to a higher place, when yous are not specifying a key or securekey, this will only work for the aforementioned user on the same computer volition exist able to decrypt the encrypted string if yous're not using Keys/SecureKeys. Any process that runs under that aforementioned user account will exist able to decrypt that encrypted string on that same motorcar.
If you lot want to be able to share a credential with multiple machines/logins/etc, and so you'll need to utilize Keys/SecureKeys. I'll save that for another post.

Kris Powell
Kris was an employee at PDQ.
Source: https://www.pdq.com/blog/secure-password-with-powershell-encrypting-credentials-part-1/
Posted by: duongshateriere.blogspot.com


0 Response to "Why Might You Need To Use The Service Password-encryption Command? What Does It Encrypt?"
Post a Comment